Nmap (“Network Mapper”) is a free and open source utility for network discovery and security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and official binary packages are available for Linux, Windows, and Mac OS X.
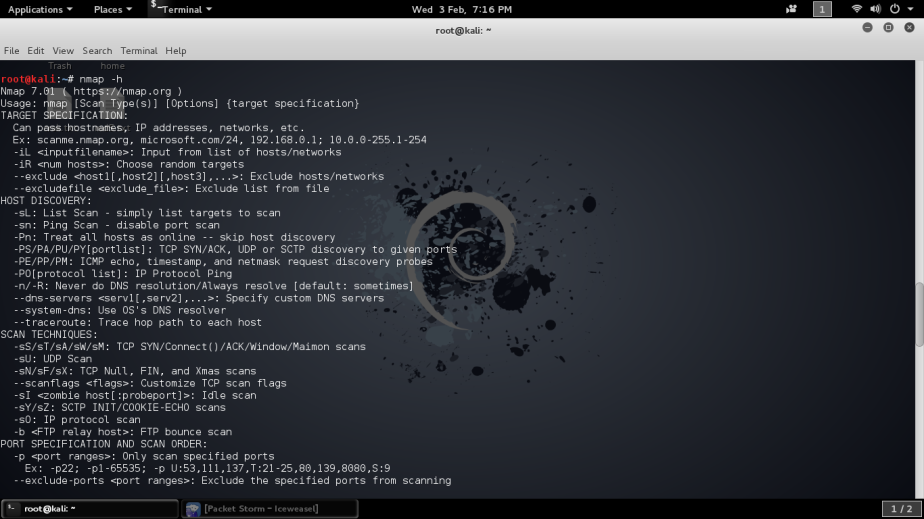
I’m going to show how to scan your own network using Nmap with these simple steps. Take note that Nmap is already installed in Kali all you need is type the following to list all commands.
- nmap -h
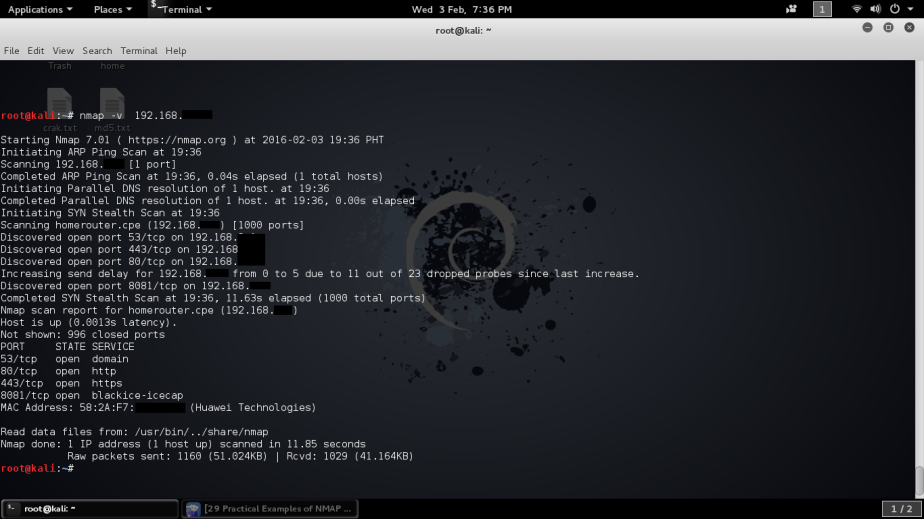
Let’s scan first with -v verbose mode to gather info about the network where you can clearly see the open ports and mac address of the router. Here you can insert your target’s IP address or webpage like nmap -v 192.168.1.1 or nmap -v example.com
- nmap -v 192.168.1.1
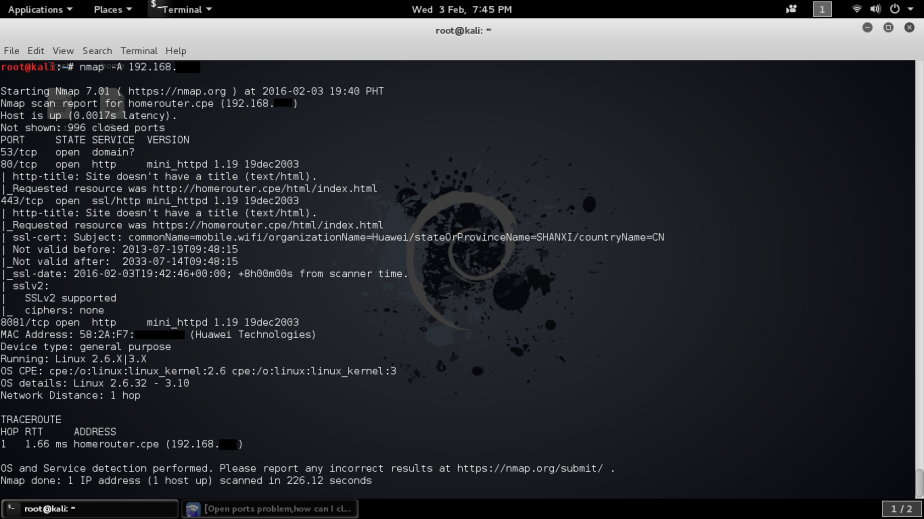
The second scan enable OS detection, version detection and script scanning, here you can see lot of information about the network, OS details, traceroute, even the router’s admin page was included.
- nmap -A 192.168.1.1
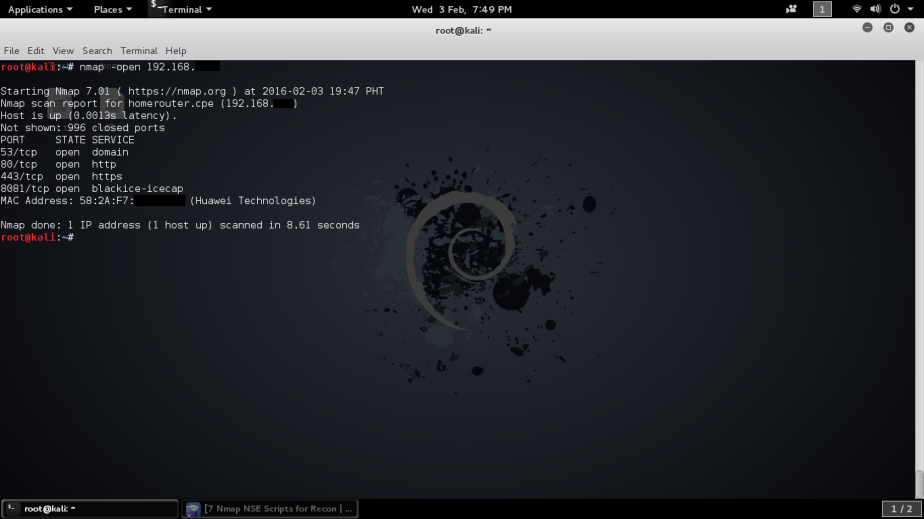
The scan to see the open ports of the router and there’s my router’s open ports – 4 in all.
- nmap -open 192.168.1.1
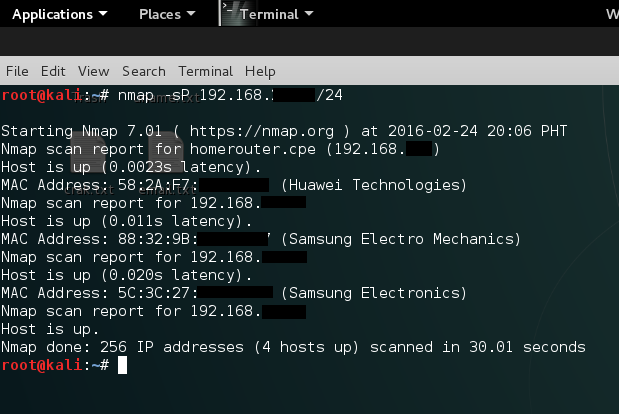
And to see the connected devices in the network type
- nmap -sP 192.168.1.1/24
Now you saw how simple Nmap commands can find important information on your target network. All you have to do is try all the commands against your network and not your neighborhood. Happy Hacking!
