Fern Wifi Cracker is a Wireless security auditing and attack software program written using the Python Programming Language and the Python QT Gui Library, the program is able to crack and recover WEP/WPA/WPS keys and also run other network based attacks on wireless or ethernet based networks.
Fern Wifi Cracker currently supports the following features:
- WEP Cracking with Fragmentation,Chop-Chop, Caffe-Latte, Hirte, ARP Request Replay or WPS attack
- WPA/WPA2 Cracking with Dictionary or WPS based attacks
- Automatic saving of key in database on successful crack
- Automatic Access Point Attack System
- Session Hijacking (Passive and Ethernet Modes)
- Access Point MAC Address Geo Location Tracking
- Internal MITM Engine
- Bruteforce Attacks (HTTP,HTTPS,TELNET,FTP)
- Update Support
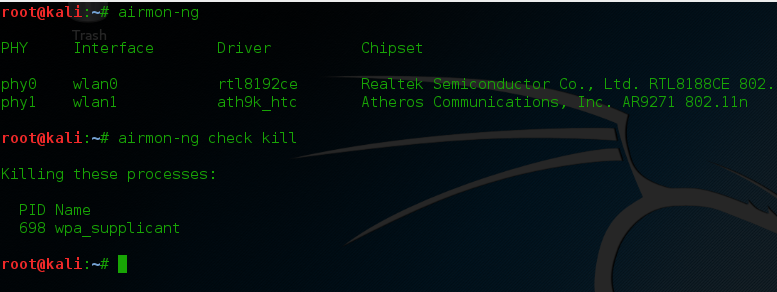
First step, make sure your card is capable of packet injection read here and here here for compatible wireless cards. If not there’s no need to follow the instructions below you’ll never crack any wifi password without using compatible cards. Then let’s check your cards interface to use type airmon-ng, mine is wlan1 with ath9k driver. After all let’s kill processes that can intervene with your cards driver type airmon-ng check kill
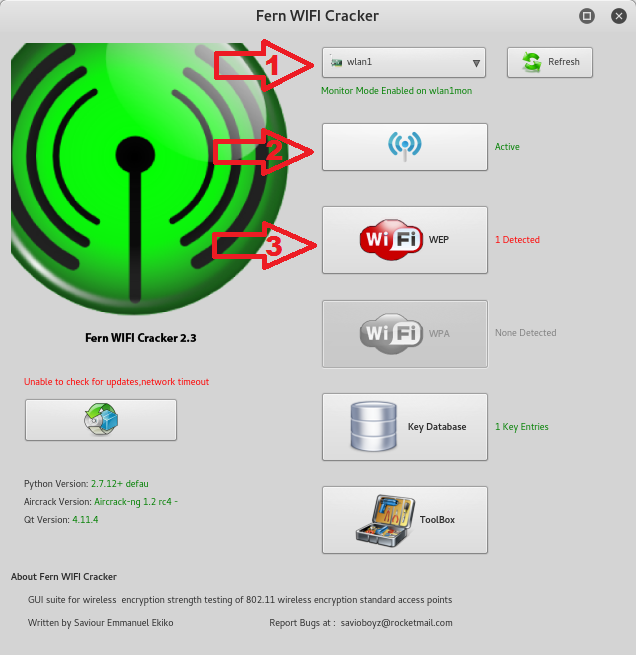
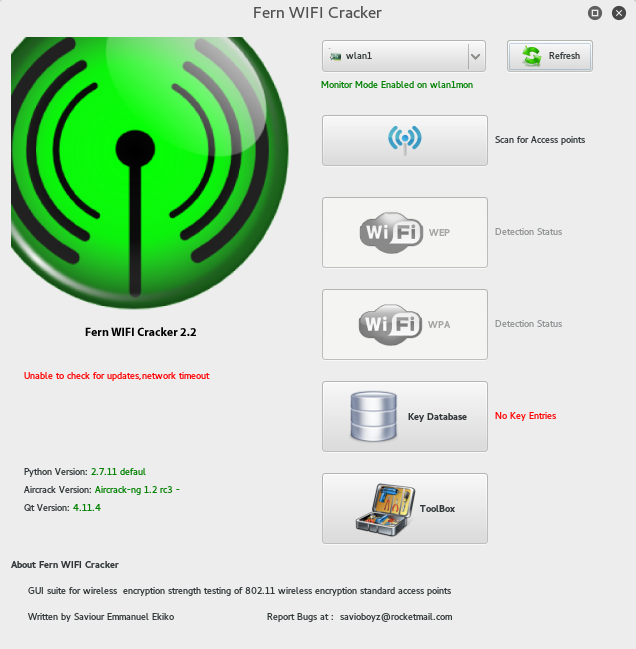
Run Fern Wifi cracker and choose from the drop down tab the wifi card it will automatically enable the card in monitor mode. See the green text Monitor mode enabled on wlan1mon.
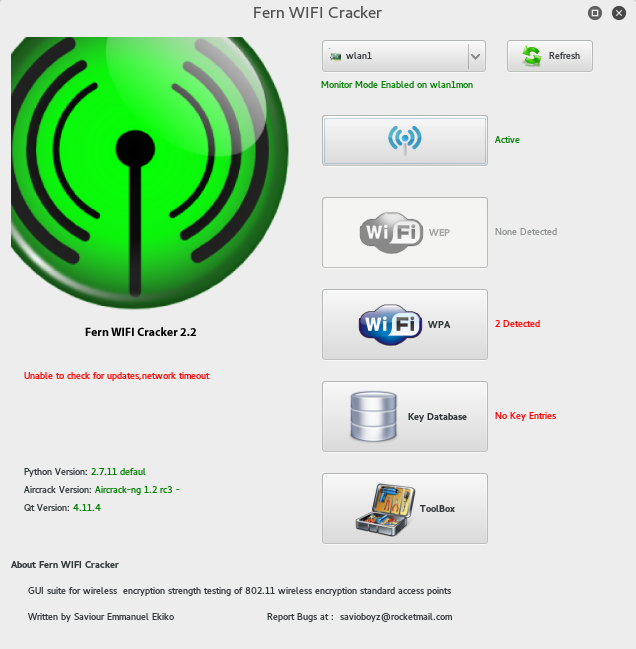
Next click the Scan for Access Points to look for target APs if it detects WEP the wep button will be highlighted if not the WPA, in my case a WPA access point was detected. Now just click the WPA button to open the attack panel where you’ll fulfill your dream of being a wifi hacker.
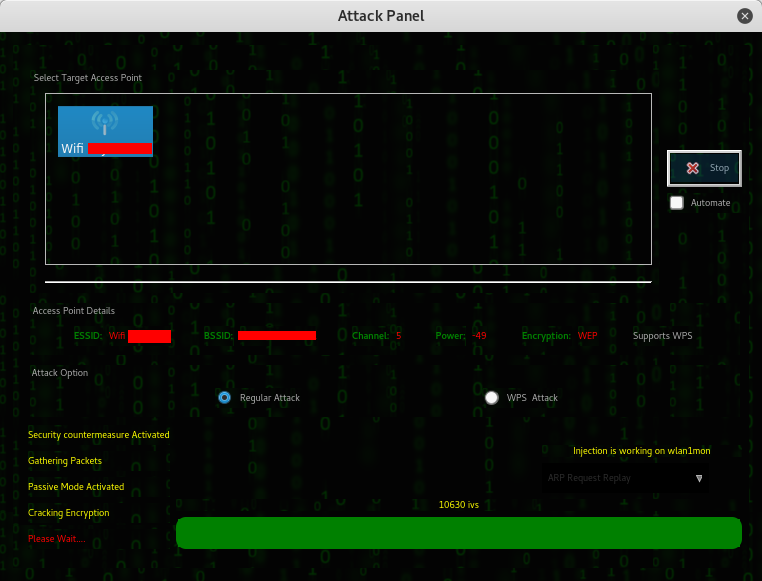
Select your target access point, tick if it’s regular or wps attack (for wps enabled routers), upload your wordlist to be used in password cracking then click Wifi attack and this tool will magically do everything for you as if you’re having magic wand.
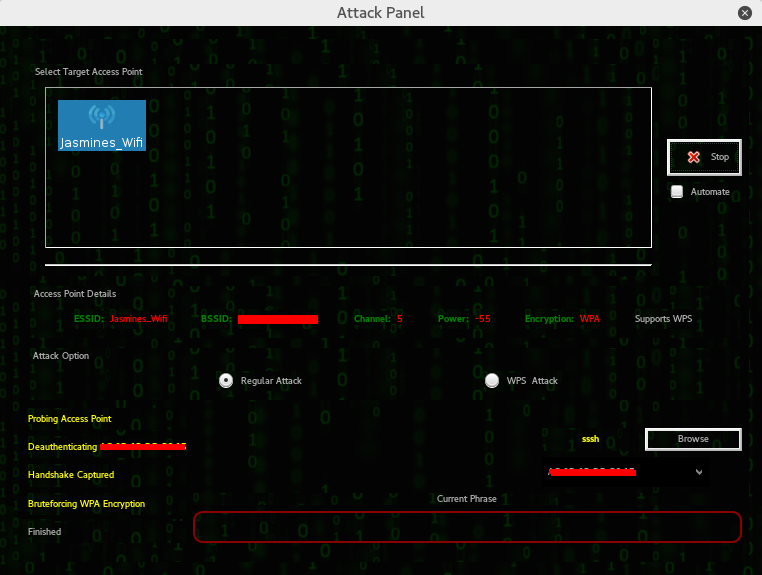
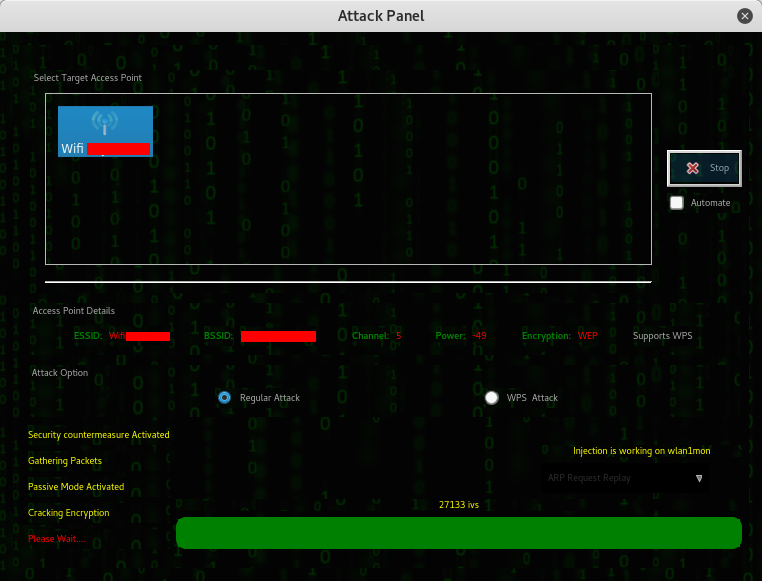
All wifi cracking tools follow these steps – deauth connected clients, capture the handshake and crack the password against your wordlist – wait! here’s the catch, if your wordlist contains the password you can get the password, if not, either get a bigger wordlist or buy faster machine that can bruteforce it without relying on wordlist. The length of time cracking WPA/WPA2 depends on how big is your wordlist and your luck, unlike cracking WEP which depends on IVs captured.
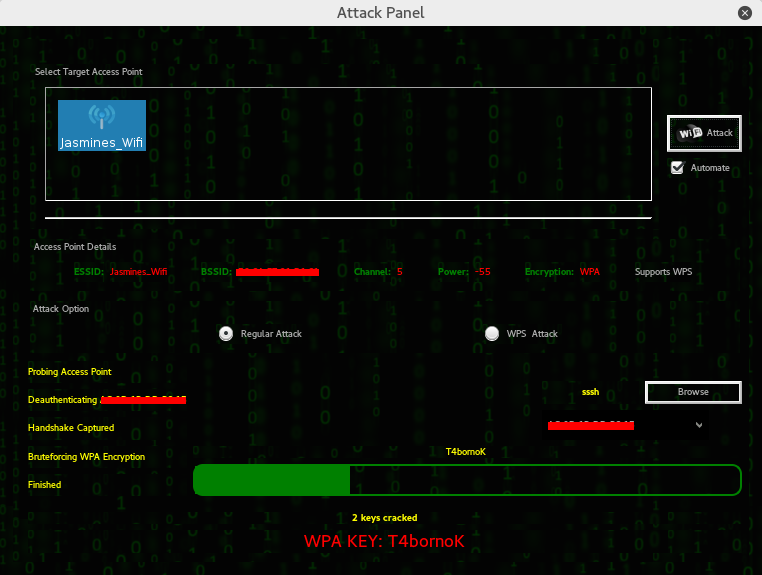
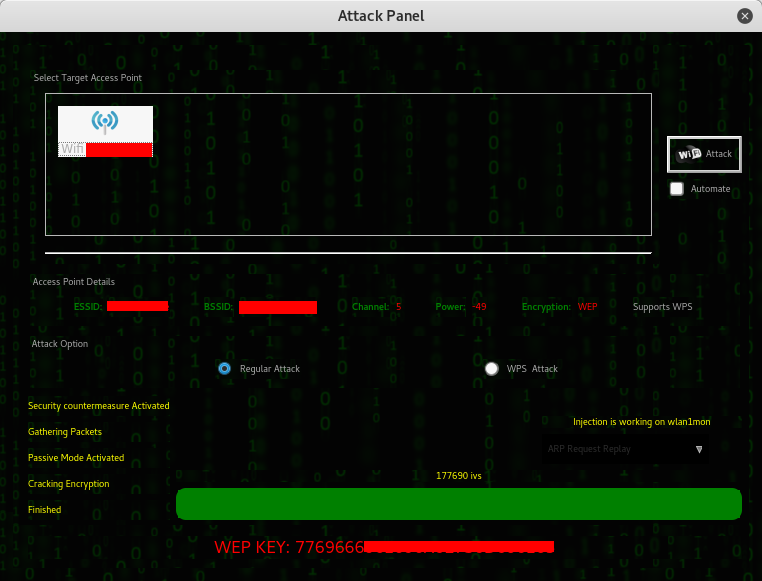
That’s it, the WPA password! There’s a lot of tool in Linux that can crack WPA/WPA2 but Fern Cracker is the easiest to use, thanks to its user friendly GUI.